Pseudonymity and the billion-user table
A single, giant users table for the whole internet is privacy-preserving
There was a specific type of response to my previous post on the blockchain-as-users-table that I got from a handful of smart readers. This response is based on a misunderstanding of the technology and its possibilities, but it's not a dumb or ill-informed response by any measure, and indeed my post practically invites it.
I could summarize that response like this: By centralizing everyone's identity into a single, searchable data structure, the blockchain will explicitly give advertisers what they've been trying to build in secret all along, i.e., a way to track each user across multiple platforms. If we want to avoid surveillance, we should be doing the opposite of building what is in effect a multi-billion-row users table for the entire world to put their identity on.
This response follows directly from my post's discussion of the classic users table, where there's a one-to-one mapping between rows and users — only one user per row, and only one row per user.
But identity on the blockchain doesn't work this way. Instead, the blockchain (with multisig) makes it possible to do many-to-one, one-to-many, and many-to-many mappings between users and wallets (i.e. the blockchain's equivalent of a users table row).
I want to focus on one-to-many specifically because this mapping has the most important near-term practical implications for on-chain identity. Specifically, what I'm describing here is pseudonymity, which the blockchain makes fairly frictionless.
With a software crypto wallet, it's trivial to generate a new on-chain identity that lets you receive money (or messages, or both). That identity is just a public/private key pair, and you can make as many as you care to juggle and use.
Each of these identities is a pseudonym that you can use to send and receive data on-chain. To the extent that you can manage these pseudonyms and protect them from getting stolen, you can use them to access any services that are built on the blockchain where these identities reside.
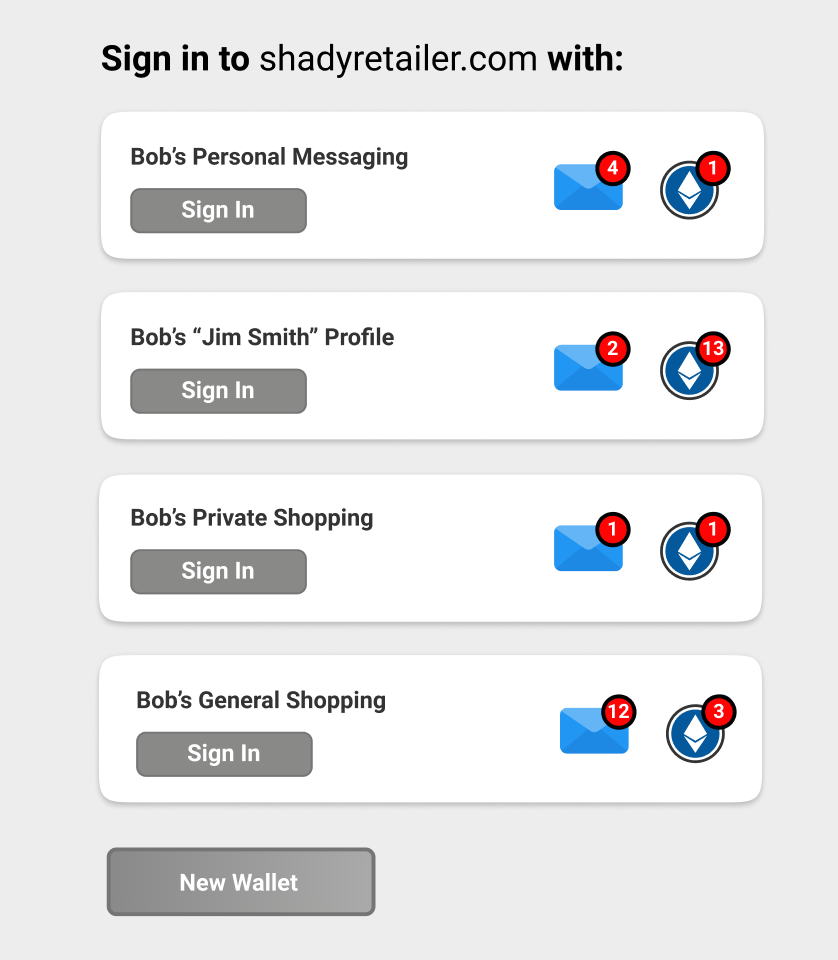
This is the kind of thing that makes a lot more sense with a concrete example. We're all familiar with the social log-in boxes that let you sign in to many websites:
Imagine a user flow where instead of seeing these boxes, you clicked a "Log in with Ethereum" box that then connected to a browser-based local wallet and gave you something like the following screen:
Each of the above identities is just a locally generated key pair that has some on-chain data associated with it -- in this case some messages and some money.
Since these identities exist on this particular browser installation, you could create, update, or delete them locally, or you could copy them to another browser. But ultimately, you could log in with one of these in order to use the service, including sending and receive payments and messages at whatever identity you use.
Furthermore, any credentials, money, messages, endorsements, or other data (or social capital) you collect on-chain under this identity would follow you to any service that accepts this log-in.
(Of course, you could implement much of the above in a centralized fashion by combining single-use email service with a single-use credit card service, but this implementation has far more friction in terms of getting up and going a simple wallet installation.)
The security and privacy benefits of the above should be immediately apparent.
No more tracking you from service to service, unless you want it.
No more worrying about if your log-in data was compromised in the latest massive hack to hit the news.
You own your data and your identity, and you can slice and dice it into as many different forms as you want.
Think of the above image almost like a wardrobe, where each wallet is a different outfit you can put on to go to a different venue. Just like you wear one set of clothes to the gym, another to a nice restaurant, and another to work, you'll reach for different wallets for different kinds of online activities.
The downsides are bad, but already mitigated
We do have to be real about the potential downsides of the above scheme because they're no joke.
First, if Bob's "Jim Smith" pseudonym gets linked with Bob and he's outed under that identity, there's no undoing that. Everything that Bob did under that identity that left traces in whatever third-party database is now owned by Bob into perpetuity.
So the risk of getting blown up is real, but it doesn't strike me as materially worse than the risk of having any other alt or sockpuppet account blown up on a centralized service.
Then there's the risk of theft. If Bob's laptop gets stolen and the passphrase that protects those wallets is compromised, then the bad guy has those identities and can impersonate Bob with impunity. There is nothing Bob can do about this -- no number to dial to get it turned off or regain control of the identities. Whoever has those keys is Bob, as far as the blockchain (and everything connected to it) is concerned.
Related to the above is risk of loss. If Bob's laptop crashes and his keys aren't backed up, or if he deletes a wallet and then regrets the deletion, there is no account recovery option.
So that's the bad news. The good news is that all of these problems have already largely been addressed by crypto's robust wallet and identity management ecosystem. When the login box in the previous section becomes a reality, you'll be able to tun the privacy/custody/centralization tradeoffs to suit your own risk profile and needs.





Maybe I'm also misunderstanding something, but it seems that having your crypto identity tied to your real identity is worse than having your "sockpuppet" account tied to your identity: your crypto transaction history is public domain, while your creditcard statement is private